 Lately, I have been writing a lot about visibility. In business, there are layers and walls that stack next to each other. Although sometimes you may have a visibility within one perspective, a limited view can still mean a blurry big picture. Last week, I talk about CEM’ing in the mobile space. I talked about Tealeaf’s ability to create more of a real-time management concept. More specifically, this week I wanted to cover a topic that brings you one step closer to a successful and secure Bring Your Own Device Mobile Enterprise.
Lately, I have been writing a lot about visibility. In business, there are layers and walls that stack next to each other. Although sometimes you may have a visibility within one perspective, a limited view can still mean a blurry big picture. Last week, I talk about CEM’ing in the mobile space. I talked about Tealeaf’s ability to create more of a real-time management concept. More specifically, this week I wanted to cover a topic that brings you one step closer to a successful and secure Bring Your Own Device Mobile Enterprise.
When it comes to securing cross-platform communications and company owned assets, most companies have some kind of plan that has been in place for awhile. However, adapting to new mobile implementation sets a new stage for techniques to secure your devices — especially employee owned ones. Within the IBM Mobile Foundation, there is an important piece that defines a new way build your visibility between you and your employees. It is IBM’s Tivoli Endpoint Manager (TEM).
By now, many will have heard of TEM and have heard of some of its functionality. However, I doubt many have really seen the power that it provides within your enterprise. Tivoli Endpoint Manager for Mobile device management is one piece of a time-tested endpoint management system. It has provisions to gather all devices (laptops, desktops, mobile devices, etc) into one pool of command and control. Tivoli Endpoint Manager is essentially a command center for visibility. It has the ability to identify connected devices uniquely, update and control features of those devices, and even monitor their device statuses and control options. Within the mobile realm, you can even gain visibility into your employee’s devices.
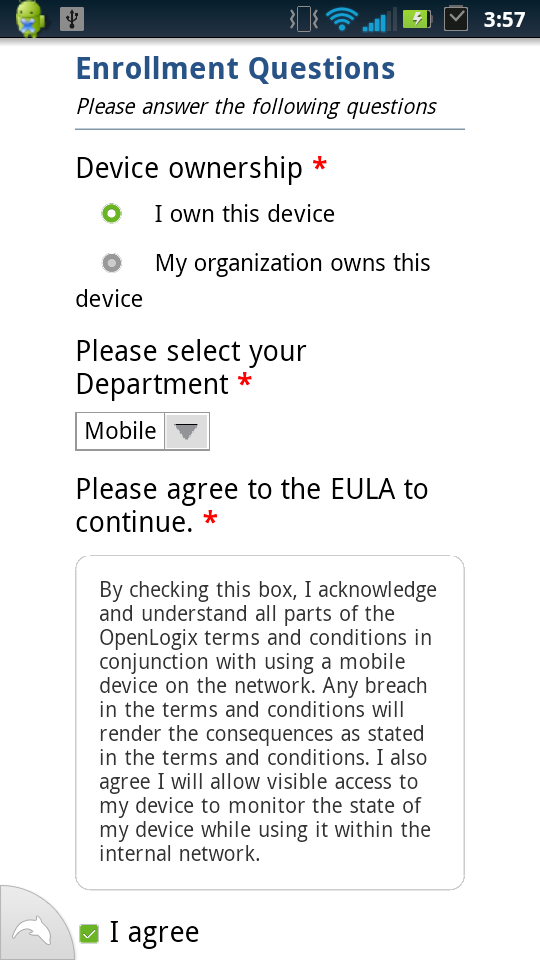
When bringing in a personal device, there are many security risks that follow. With TEM, you have the ability to custom enroll your employee devices utilizing authentication (LDAPS or other Identity Managers). From there, you have to ability target single devices and control/monitor its use. Adding security policies like screen-pin requirements, remote wiping, and analyzing a device’s current apps are pretty straight forward.
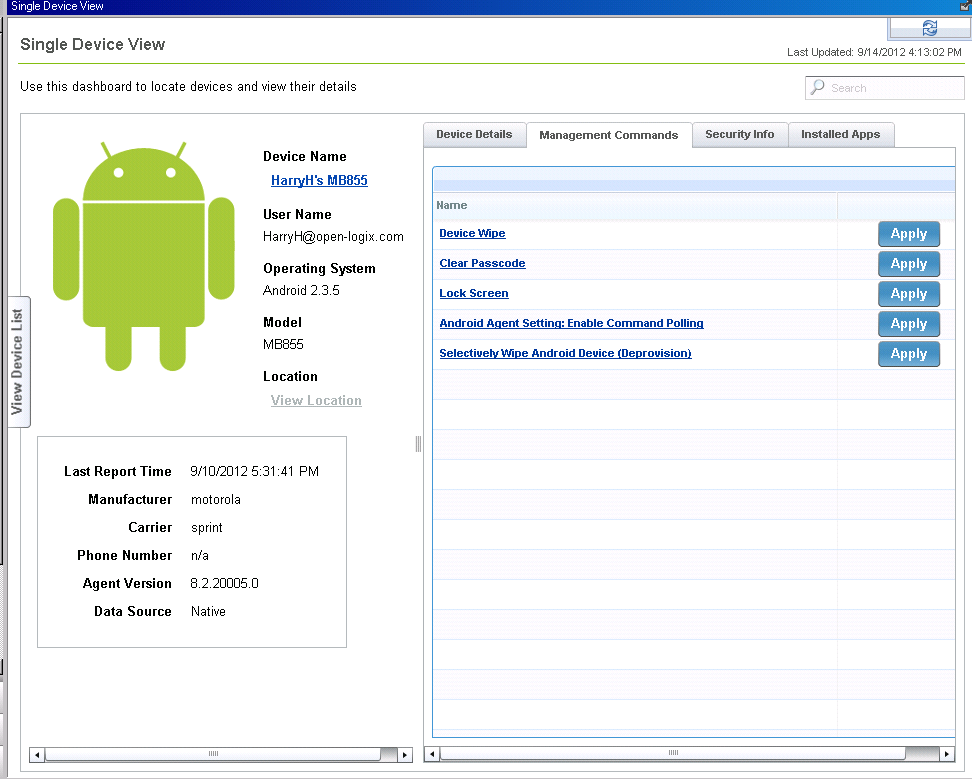 Beyond the scope of just a single device, there is also a web-reporting tool to build custom reports. For example, you could create a chart based on what percentage of users are currently meeting password policies. From there you could build a strategy to help enforce or adapt the password policy.
Beyond the scope of just a single device, there is also a web-reporting tool to build custom reports. For example, you could create a chart based on what percentage of users are currently meeting password policies. From there you could build a strategy to help enforce or adapt the password policy.
Device management is one of the biggest concerns for mobile enterprises. Not being able to see what your employees are doing, especially with their personal devices, can lead to security breaches. I am not saying that you shouldn’t trust your employees. If anything, this should empower them by providing them another asset that they own. However, there should always still be measures in place to protect your companies assets (to include your employees).
IBM Mobile Foundation is a mixture of Mobile Enablement tools. Tivoli Endpoint Manager helps solve some of the problems that come with this new phase in enterprise. To reference the Balance Wheel from my post a few weeks ago, a powerful tool like TEM helps balance the other sides of the Mobile Enterprise Wheel.



